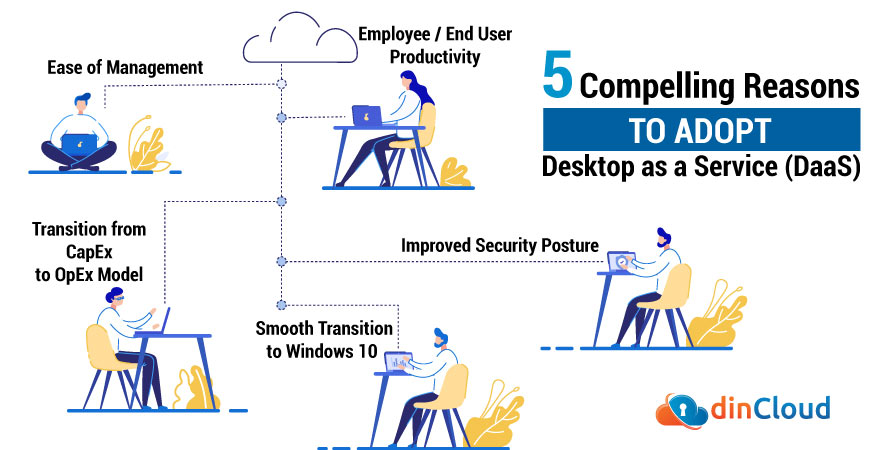
Things about Daas Desktop As A Service
Daa, S provides online applications as well as desktop computer services by means of a public or exclusive cloud solution. Your workforce can access this service via a web link using an html-based web internet browser or a safe and secure application downloaded to a gadget such as a laptop, desktop, thin customer, smartphone, or tablet computer. Daa, S is supplied as a subscription solution as well as is multitenant in nature.
The Daa, S supplier then streams the virtual desktops to the client's end individual gadgets. Daa, S suppliers take care of the VDI deployment along with maintenance, safety, upgrades, information back-up, as well as storage space. And also the consumer handles the applications as well as desktop computer photos. Daa, S is a good option for organizations that don't wish to spend in and also handle their own on-premises VDI solution.
Daas Desktop As A Service Fundamentals Explained
7% between 2019 and also 2026. Daa, S represents desktop computer as a service. It describes a type of digital computer that offers remote or mobile employees with cloud work spaces. Making Use Of Daa, S, workers can connect to an online work area that runs in the cloud using whatever tool they have.
Getting My Daas Desktop As A Service To Work
— Cloud Links (@ldcloudlinks) December 15, 2022
A recent record by the Citrix Service Company Of Quality revealed that the Daa, S market has "matured and evolved" in recent years. The primary advantages of desktop computer as a service are: Adaptability, Lowered upkeep prices, Protection, With Daa, S, firms can offer a work area to new workers without needing to stress over provisioning hardware or bothering with individual setups.
He notes "Secure digital desktop computer framework (VDI) and also desktop-as-a-service (Daa, S) links have become a concern over the last two years, given the fast development of online meetings, remote training sessions, and also sales phone calls. my blog VDI/Daa, S aids stop online sessions from being hijacked while safeguarding the identification of every online participant without destruction in bandwidth."Using Daa, S suggests businesses can implement Bring Your Own Tool (BYOD) plans and also allow employees to function from anywhere. DAAS Desktop as a Service.
No company information ends up on individual devices. Daa, S implementations can lower the risk of such strikes by developing sandboxed Windows atmospheres.
Daas Desktop As A Service Can Be Fun For Anyone


In some means, Daa, S might sound a great deal like digital desktop computer infrastructure (VDI). There's one vital distinction in between Daa, S and VDI.With VDI, organizations utilize on-premise servers that are kept by in-house groups.
For numerous firms, the expense of managing that facilities in-house is prohibitive. Daa, S makes use of cloud-based online desktops.
"Digital desktop infrastructure is provided through on-site modern technology remedies and also requires a hardware pile kept by IT administrators. Legacy VDI solutions are complex tools.
Rumored Buzz on Daas Desktop As A Service
This number takes into account the price of getting and also applying every one of the required framework. Among one of the most substantial benefits of including a Daa, S version is cost-saving. With legacy IT, services need to buy a continuous license for each desktop and also every laptop in usage by the business.
Daa, S additionally conserves companies money on safety, technological support, as well as upkeep., included that a Daa, S system can be "quickly and also promptly" provisioned to meet your needs.
It's very easy to include and also eliminate accounts based on company demands. Lots of suppliers provide versatile rates.
The Best Guide To Daas Desktop As A Service
And also, you don't need to bother with equipment failure, simply since the system is cloud-based. For a company that has a mix of office-based and also remote workers, took care of cloud services and remote desktop computers can be an effective resource. They enable remote employees to log in to a safe environment where they have accessibility to every one of their performance applications and info.
There's no need to spend a whole lot of money more info here on costly hardware to access their systems. DAAS Desktop as a Service. Spending in a Daa, check this S option can be affordable for several firms, yet the incorrect service can lead to higher-than-expected costs, as highlighted in this research by Business Strategy Group. Because of this, it is essential to choose a Daa, S supplier that uses clear prices that makes good sense for your usage case.